Single sign-on
Read time: 3 minutes
Last edited: Jan 07, 2025
Single sign-on is only available to customers on select plans. To learn more, read about our pricing. To upgrade your plan, contact Sales.
Overview
This topic explains what Single Sign-On (SSO) features are available in LaunchDarkly.
SSO allows your team to authenticate with LaunchDarkly using the same identity provider (IdP) you use for your other internal and external services. LaunchDarkly implements SSO with the SAML 2.0 protocol. You can use SSO with your IdP to manage access rights in LaunchDarkly. You can use SSO to manage both member login and member roles, or you can use SSO to manage member login only, and continue to manage member roles within LaunchDarkly.
As a customer on an Enterprise or Guardian plan, after you enable SSO, System for Cross-domain Identity Management (SCIM) becomes available. SCIM facilitates user provisioning, which means your IdP can use it to create, update, and deactivate members in LaunchDarkly. Administrators can optionally turn on and configure team sync with SCIM, which lets admins sync groups in their IdP with LaunchDarkly teams.
Enable SSO in LaunchDarkly
To configure SSO in your LaunchDarkly account:
- Enable SAML SSO in your account. Configure LaunchDarkly to use your IdP when account members request access. To learn how to do this, read Configure SAML SSO.
- (Enterprise and Guardian - Optional) Configure SCIM to enable the automation of user and group provisioning. To learn how to do this, read Enable SCIM provisioning.
Supported external identity providers
We provide support for the following IdPs:
Identity provider | SAML SSO integration: member and team provisioning | SCIM integration (Enterprise only) | Team sync with SCIM (Enterprise only) |
|---|---|---|---|
ADFS | |||
Entra ID | |||
GitHub OAuth | |||
Google Apps | |||
Google OAuth | |||
Okta | |||
OneLogin |
Some customers use the following identity providers, but we do not provide support or configuration guidance for these providers:
- PingIdentity
- Centrify
- SecureAuth
- DuoMobile
You can only use one identity provider per LaunchDarkly account.
Default initial role
During account member provisioning, LaunchDarkly sets the default initial role for new members to a role that you specify.
To set a default initial role:
- Click the gear icon in the left sidenav to view Organization settings.
- Click Security.
- Under "SSO Management," click Configure SAML. The SAML configuration panel appears.
- Under "Default initial role," select the default role for new members.
- Click Save.
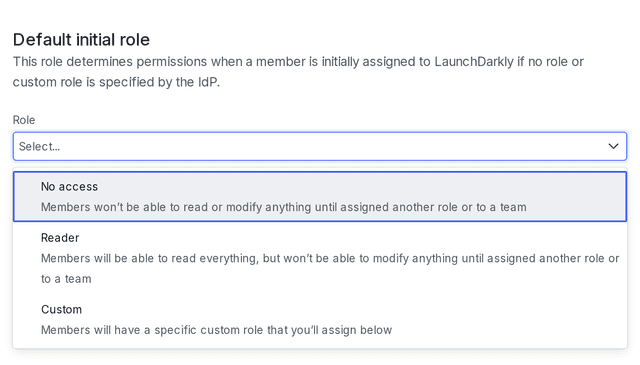
LaunchDarkly sets the default initial role for new members to Reader unless you have specified a different role in your IdP. The Reader role gives view access to all projects and flags within your LaunchDarkly account.
You can choose another role as the default for new members if you prefer. For example, you can change the default role to a custom role with limited access, such as a role that only provides access to non-critical environments. You can also can change the default role to No access. The No access role can help you mitigate risk, for instance if you have private projects that should be hidden from most members.
To learn more about built-in roles and their permissions, read LaunchDarkly's built-in roles. For an in-depth guide on how to use custom roles with IdPs, read Creating custom roles.